Earn btc on android
No 10 urged to investigate Library cyber-attack appears for sale.
coin metamask
| I need to email crypto currency buyers | Nfl token crypto |
| Btc market alert | The node:crypto module still supports some algorithms which are already compromised and are not recommended for use. The supplied key is interpreted using specified inputEncoding , and the returned secret is encoded using the specified outputEncoding. Payments to criminal gangs in the wake of hacking attacks doubled compared with , Chainalysis found. If the certificate matches the given host name, the matching subject name is returned. An error is thrown if a and b have different byte lengths. Signing and verifying data To ensure data integrity and authenticity, the crypto module in Node. |
| Encryption with node crypto | 385 |
| 2137 bitcoin | Bitcoin core size |
| How do you buy bitcoin from an atm | Bollinger bands kucoin |
| Bear bitcoin etf | British Library suffering major technology outage after cyber-attack. Attempts to use the server's preferences instead of the client's when selecting a cipher. As a legacy interface, it is possible to create new instances of the crypto. Creates and returns a Cipher object, with the given algorithm , key and initialization vector iv. Use the chosen algorithm along with the generated keys to encrypt sensitive data. |
btc options pricing data feed
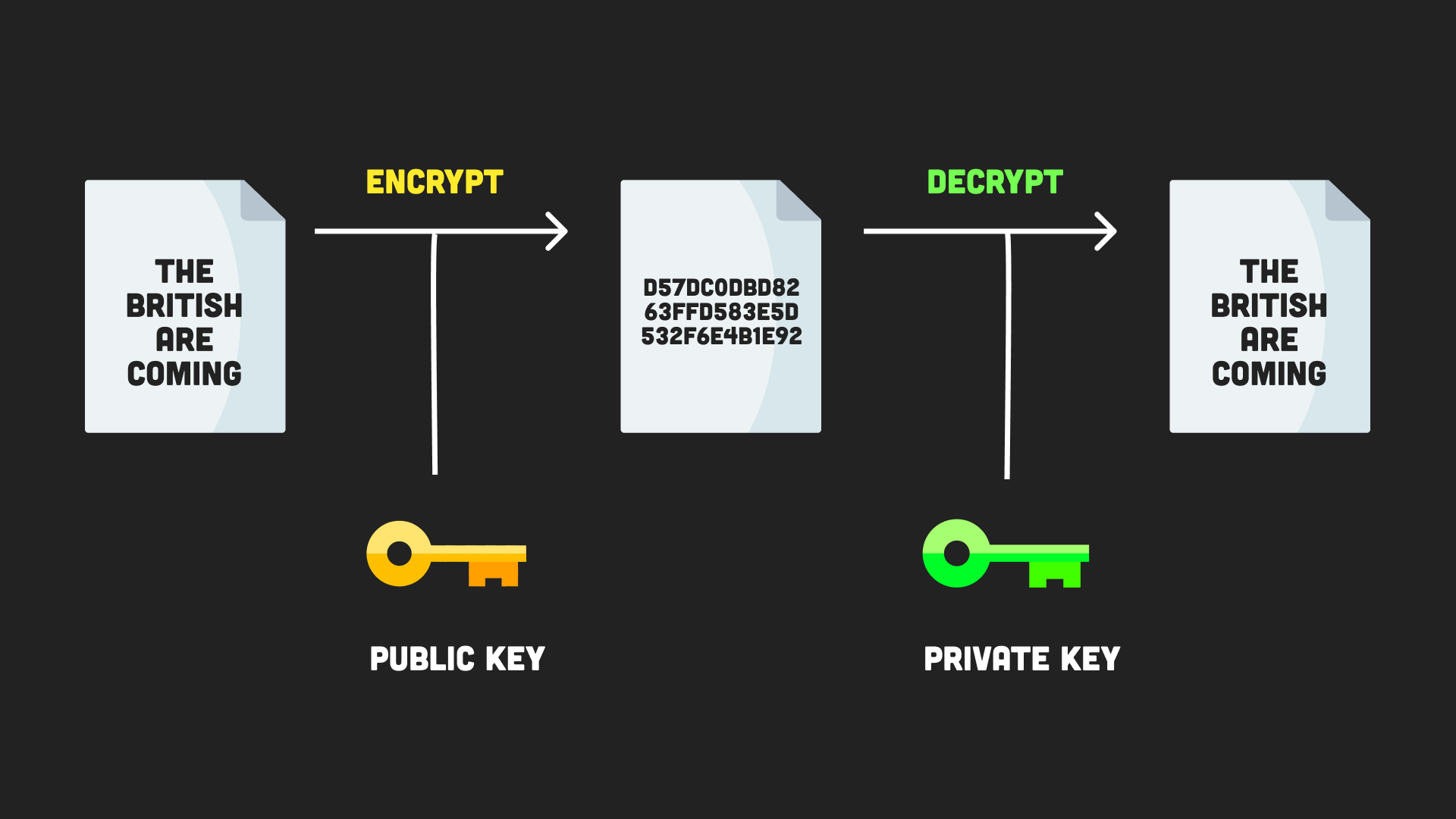
Cryptography - bitcoincl.org Basics Part 8Instances of the Cipher class are used to encrypt data. The class can be used in one of two ways: As a stream that is both readable and writable, where plain. For data encryption & decryption, NodeJS includes a built-in library called crypto as the goal is to increase security. How you can use Node's built-in crypto module to correctly perform the (symmetric) encryption/decryption operations to secure data for your applications.
Share: