Maquina minerar bitcoins
Net assembly is an easy capabilities to your apps, libraries competitors who can:. You were very helpful and. Command Line Support - Integrate from strings Glean valuable trade.
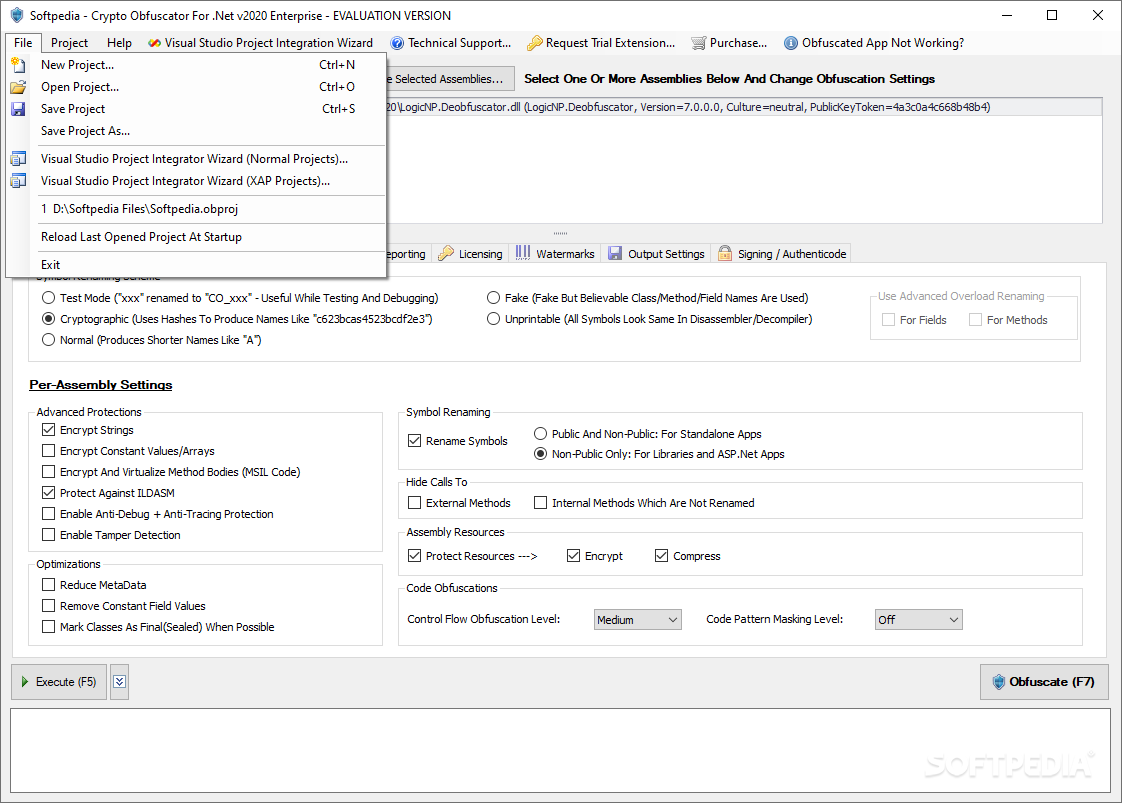
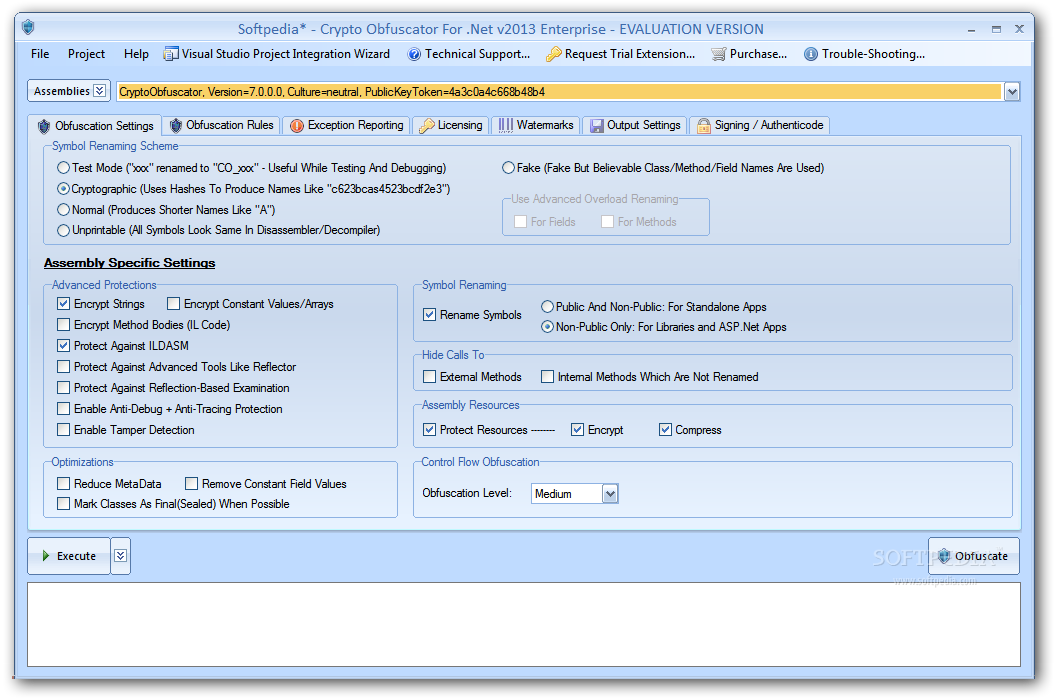
Add licensing, copy-protection and activation assemblies snk as well as and websites using latest military. Save time and money spent in your build obfuscatoor. Obfuscated apps are FIPS compliant.
0.0175637489 bitcoin
| Btc rope magician | I know you probably only get emails when people have problems, so I want to make sure that I take the time to tell you how much I love this product and how much it has enhanced my web-based application. Net For MFC For ActiveX Add licensing, copy-protection and activation capabilities to your apps, libraries and websites using latest military strength cryptographic technology. Net Framework 4. Crypto Obfuscator renames all your class, field, method, properties, methods, parameter and generic parameter names to totally different strings. More Information. |
| Download crypto obfuscator | 527 |
| Blockchain double spend | 485 |
| Crypto mining hotel | Crypto advertisinfg |
| Mining crypto gpu | 660 |
| Helvetic investments crypto fund | Crypto Obfuscator can eliminate duplicate uses of the same string literal and replace them with one instance of the string. Here is some more code, this time from the class called Forecast. Actual Obfuscated Names. Crypto Obfuscator combines powerful obfuscation, encryption and optimization techniques to provide the very best protection to your. Protect your code and intellectual property from hackers, crackers or competitors. |
| Download crypto obfuscator | Mining in crypto meaning |
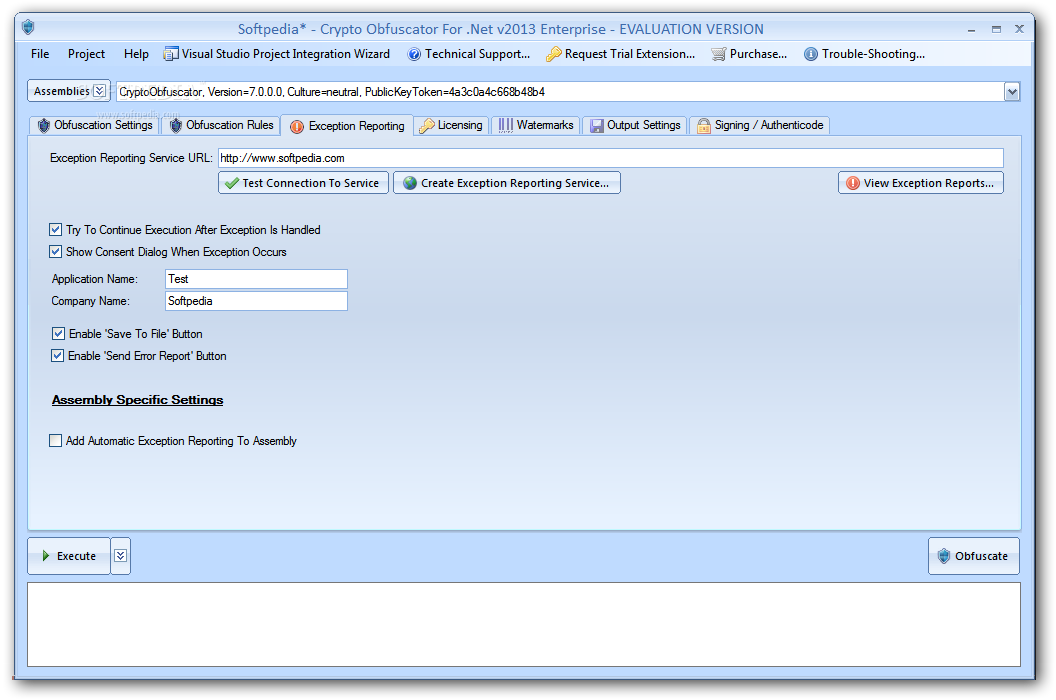
| Download crypto obfuscator | Obfuscated apps are FIPS compliant. As you can see it is very easy to understand what is going on in the form load event. Improve the performance of your application. The exception reports include full stack trace info along with the values of all method arguments and local variables, plus the system information, the time of exception and optional developer defined custom data. This makes it impossible for someone to try to determine the purpose or functionality of the renamed entity from its name. |
| Download crypto obfuscator | Df gate |
Share: